How we can make a web application a fix entryway. As I comprehend a web application is an entryway accessible on web for the overall population who can without much of a stretch utilize it emphatically for various reason or for the explanation the web application testing exists.
You should know, web applications are the obvious objective for programmers to obtain entrance since it is freely accessible, and a programmer has to know just the name of the association which he needs to hack. Helplessness is the shortcoming or absence of control exists in the application. Vulnerabilities can be because of shaky programming in web applications, absence of access control puts or designed, miss setup of uses and server or because of some other explanation, there is no restriction.
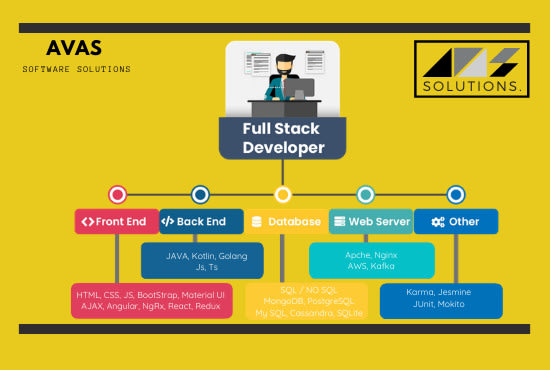
There are numerous approaches to solidify your web application or your web server we will examine this in some time. We should perceive what are the key prerequisites which makes up a web application live.
- a. Web Server
- b. Application content showed
- c. And additionally databases
- These are the key segments of any web application.
Web server is an assistance which runs on the PC and serves of web content/application content. This server commonly tune in on port 80(http) or on port 443(https). There are many web servers which are unreservedly accessible or business including top givers
- a. I.I.S by Microsoft
- b. Apache by Open source network
- c. Tomcat and so on
Application content is the thing that you see on the site, it tends to be dynamic or static, powerful substance containing web applications are at more hazard as contrast with static substance containing web applications. Dynamic substance containing web applications utilizes database to store the evolving content. This database can be one of the accompanying sorts.
- a. MySql Server
- b. SQL Sever
- c. Prophet Server
- d. MS Access or some other
We have talked about a great deal on web application engineering now I will tell you the best way to perform infiltration on web application (what we state a Pen-test).
Data Gathering
Any pen-test can not be practiced without playing out the data gathering stage. This is the stage which is the core of pen test, there are numerous approaches to do data gathering lets talk about here.
Hacking with Search motors.
I would not list explicit web index which can be utilized in data gathering stage, there are loads of web index which are more force full from which mystery/secret data can be accumulate. There are procedures which you can use to accumulate data on the objective.
For instance
You can utilize ‘inurl:’ in web crawlers to recognize what are the finished webpage guide of the web-based interface, you can likewise utilize intitle: administrator to access the administrator board of the web-based interface, you can utilize inurl: Admin filetype: asp or aspx so as to look for administrator login pages or essentially you can bolt for login page for any entryway.
You can likewise search for the email address of the specialized staff, email address shows the client id for that particular individual. You can likewise utilize files for more data to assemble. This is the short rundown of the systems, to clarify more I would compose a book
Assaults
Here I will clarify you what are the significant assaults which programmers use on web applications or the assaults which are hazardous for web applications. We will just talk about application level vulnerabilities and assaults.
On the off chance that you are a specialized individual your need would be accessibility of your server, you ought to be approached by your senior administration for the 100% up time of your server, this is where specialized staff left security openings in the arrangement just to make it live or so as to surrender 100% time as coordinated. This miss design may prompt the trade off of the total server.
SQL Injection
A high appraised assault which can prompt total web server bargain or complete regulatory level access to programmer. SQL is an inquiry language which developers use for question the substance from database in powerful web applications. Commonly a less experienced software engineer left bugs in applications which if aggressor found can be extremely destructive.
SQL infusion assaults happens due shortcoming in input approval, unreliable programming or because of shaky web application engineering. SQL infuse can be utilized to by pass logins, gain administrator level access, can be destructive if a programmers access administrator logins. SQL Injection ‘Association’ assault is regularly utilized in unique web applications infiltration testing. There is more stuff which can be composed on sql infusion, I think this information is all that anyone could need at this stage.
CSS/XSS (Cross site scripting)
XSS/CSS is a customer side defenselessness which can be utilized in phishing assaults. Numerous programmers use XSS so as to increase mystery data which can be Mastercard numbers, login passwords, private data and the sky is the limit from there. As XSS runs on customer’s program programmers use to embed contents so as to accumulate data from client. In the event that XSS utilized in phishing assault it very well may be profoundly evaluated powerlessness.
Be Cure
Exclusively On Fiverr By amilcshanakan

To be fix finished evaluation of web application ought to be acted so as to test the application and make it bug free, consistent testing ought to be kept up. Info approval ought to be executed. Default arrangements ought to be expelled or changed, secure database availability ought to be kept up and in keep going index posting on each catalog ought to be killed, document authorizations ought to be assessed, get to rights should be kept up. To know more visit the official website http://bit.ly/3a6nr2D